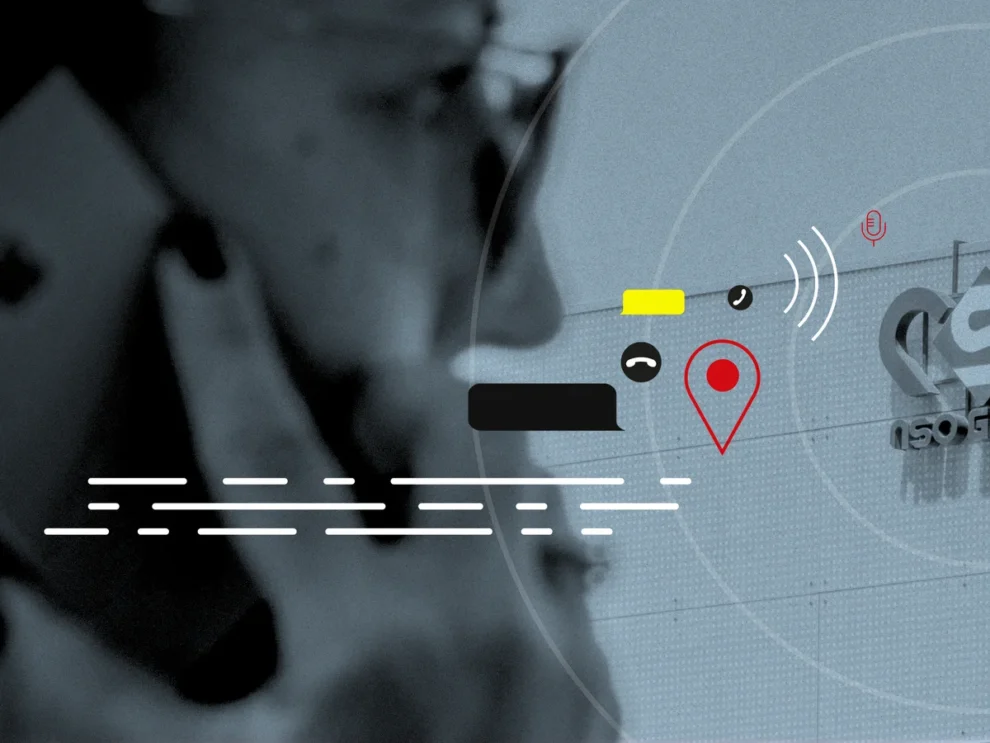
For years, a shadowy network has been quietly distributing malicious Android apps, potentially compromising the privacy and security of countless users. This isn’t a new phenomenon, but the scale and persistence of this particular operation, and the fact that it’s allegedly linked to a known spyware developer, are raising serious alarms. This article delves into the details of this disturbing trend, exploring the who, what, when, where, and, most importantly, the why behind this pervasive threat. We’ll examine the methods used, the potential consequences for victims, and what can be done to protect yourself from falling prey to these insidious apps.
The story unfolds like a digital thriller: A spyware company, allegedly implicated in the creation and distribution of these malicious apps, has been operating in the shadows for an extended period. These apps, disguised as seemingly harmless utilities or games, secretly install themselves on unsuspecting users’ devices. Once installed, they can potentially exfiltrate sensitive data, track location, intercept communications, and even grant remote access to the device. This activity has been ongoing for years, with new apps regularly appearing and older ones being updated to evade detection. The geographical scope of this operation is global, though certain regions may be more heavily targeted. The motive, as suspected, is primarily financial gain through the sale of spyware or the data harvested from compromised devices.
Unmasking the Threat: How These Apps Operate
- Deceptive Disguise: The malicious apps are often disguised as legitimate apps, mimicking popular tools or games. They might be offered through third-party app stores or even through seemingly innocuous websites. This makes it difficult for users to distinguish them from genuine applications.
- Insidious Installation: Once downloaded, the app might request permissions that seem excessive for its purported functionality. For example, a simple calculator app asking for access to contacts or location data should raise red flags.
- Stealthy Operation: After installation, the app often operates in the background, minimizing its visibility to the user. It might hide its icon or disguise its activity to avoid detection.
- Data Exfiltration: The app can then begin collecting sensitive data, such as contacts, messages, call logs, browsing history, location data, and even banking information. This data is then transmitted to a remote server controlled by the perpetrators.
- Remote Control: In some cases, the app might grant remote access to the device, allowing the attackers to control the device remotely, install additional malware, or even wipe the device’s data.
The Spyware Connection: A Disturbing Revelation
The most troubling aspect of this story is the alleged link to a known spyware developer. These companies often operate in a legal gray area, selling their products to governments, law enforcement agencies, or even individuals. While some argue that these tools can be used for legitimate purposes, such as parental control or employee monitoring, they are frequently abused for malicious purposes, including surveillance of political opponents, journalists, activists, and even ordinary citizens.
- A History of Abuse: Spyware has a long history of being used for nefarious purposes. From government surveillance to corporate espionage, these tools have been implicated in numerous human rights abuses and privacy violations.
- The Blurred Lines of Legality: The legality of spyware is often murky, varying from country to country. This makes it difficult to regulate the industry and hold perpetrators accountable.
- The Ethical Dilemma: Even when used for seemingly legitimate purposes, spyware raises serious ethical concerns about privacy and consent.
The Human Cost: Victims of Mobile Surveillance
The victims of these malicious apps can suffer a range of consequences, from financial loss to identity theft to even physical harm.
- Financial Loss: Stolen banking information can lead to direct financial loss, while compromised personal data can be used for identity theft and other fraudulent activities.
- Privacy Violation: The unauthorized collection of personal data is a serious privacy violation, potentially exposing sensitive information about a person’s life and activities.
- Physical Harm: In some cases, spyware has been used to track and harass individuals, leading to physical harm or even imprisonment.
Protecting Yourself: Staying Safe in a Digital World
While the threat of mobile spyware is real, there are steps you can take to protect yourself:
- Be Cautious About App Downloads: Only download apps from trusted sources, such as the official Google Play Store. Be wary of third-party app stores or websites offering free or discounted apps.
- Review App Permissions: Before installing an app, carefully review the permissions it requests. If an app asks for permissions that seem excessive for its functionality, be suspicious.
- Keep Your Software Updated: Regularly update your Android operating system and apps to patch security vulnerabilities.
- Use Antivirus Software: Install reputable antivirus and anti-malware software on your device and keep it updated.
- Be Wary of Suspicious Links: Avoid clicking on suspicious links in emails, messages, or websites. These links can lead to malicious apps or phishing websites.
- Monitor Your Device: Keep an eye on your device’s performance. If you notice any unusual activity, such as slow performance, excessive battery drain, or unexpected data usage, it could be a sign of malware.
- Consider a VPN: A Virtual Private Network (VPN) can encrypt your internet traffic and help protect your privacy.
- Regularly Back Up Your Data: Regularly back up your important data to a secure location. This will help you recover your data in case your device is compromised.
- Stay Informed: Stay informed about the latest mobile security threats and best practices.
The Road Ahead: Combating the Spyware Threat
Combating the spyware threat requires a multi-pronged approach, involving law enforcement, technology companies, and individual users.
- Increased Law Enforcement Efforts: Law enforcement agencies need to dedicate more resources to investigating and prosecuting spyware developers and distributors.
- Industry Collaboration: Technology companies need to work together to develop better detection and prevention tools.
- User Education: Educating users about the risks of mobile spyware and how to protect themselves is crucial.
- International Cooperation: Given the global nature of the threat, international cooperation is essential to effectively combat spyware.
The recent discovery of this spyware network distributing malicious Android apps is a stark reminder of the ongoing threat to our digital privacy and security. By understanding the methods used by these perpetrators and taking proactive steps to protect ourselves, we can help to mitigate the risks and safeguard our personal information. The fight against spyware is an ongoing battle, but by staying vigilant and informed, we can make a difference. We must demand greater transparency and accountability from the spyware industry and push for stronger regulations to protect our fundamental rights to privacy.